I don t think irc is in any way secure by default.
Internet relay chat botnet.
Basically botnets were created as a tool with valid purposes in internet relay chat irc channels.
These aren t typically created to.
Botnets can actually be used for good but what makes the news of course is the botnets that aren t used for good.
Botnets are also becoming a larger part of cultural discussions around cybersecurity.
They re connected computers performing a number of repetitive tasks to keep websites going.
It s most often used in connection with internet relay chat.
Serving the internet community for over two decades mirc has evolved into a powerful reliable and fun piece of technology.
Network based botnet detection is a bit more complex.
The first bots used on irc were jyrki alakuijala s puppe greg lindahl s game manager for the hunt the wumpus game and bill wisner s bartender.
Internet relay chat irc uses a client server model to provide a chatroom.
Botnets using these methods are easy to stop monitor what web servers a bot is connecting to then go and take down those web servers.
An irc bot is a set of scripts or an independent program that connects to internet relay chat as a client and so appears to other irc users as another user an irc bot differs from a regular client in that instead of providing interactive access to irc for a human user it performs automated functions.
Internet relay chat is actually incredibly insecure.
Irc traffic is also sent unencrypted meaning keywords can be detected with a packet sniffer.
Irc used servers and other computers to relay chat from sender to.
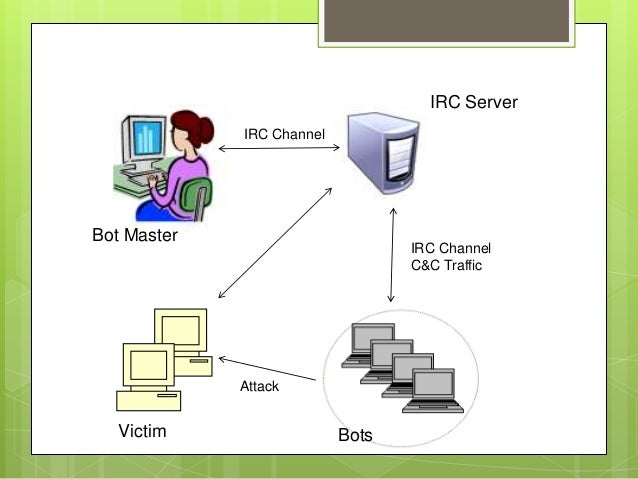
Such a server is generally known as a command and control server.
Botnets are the workhorses of the internet.
One approach lies in detecting and monitoring internet relay chat irc traffic which probably shouldn t exist on a company network at all.
These types of botnets are entirely legal and even beneficial to maintaining a smooth user experience on the internet.
C c sometimes seen as cnc cnc or cc is command and.
A brief history of internet bots.
Botnet detection on the network.
Alternately the bots might connect to an internet relay chat irc channel hosted on a server somewhere and wait for instructions.
The protocol allows users to set usernames on the server and engage in private chats or group chats via different irc channels.
One of the first uses of a botnet was to operate internet relay chat irc a completely legitimate use of connected computers.
Eventually hackers exploited the vulnerabilities in irc networks and developed bots to perform malicious activities such as password theft keystroke logging etc.
Mirc is a popular internet relay chat client used by individuals and organizations to communicate share play and work with each other on irc networks around the world.